NHS data security information and simple solutions.
On 12.05.2017 the NHS was victim to the largest cyber attack to date, a clear breach of NHS data security systems and process.
The result was mass closures of practices, and marked delays in secondary care and emergency departments. While this was a malicious act, there are some simple precautions and steps you may take to protect yourself and your organisation from similar attacks.
What are cyber attacks?
Cyber attacks are attempts by a hacker to damage or destroy a computer network or system. These attacks can take place by the following methods:
- Fraudulent emails: they are designed to look legitimate, but contain attachments or links which can cause chaos if you open them. These can also access your contact list to forward the attack to all the people you know. Common versions of this attack are also called phishing attacks which pretend to be a legitimate contact in order to get you to click a website/ enter information which is then used nefariously.
- Ransomware: malicious software that encrypts any files you have access to and demands payment. This is the type of attack that took place recently.
- Malware :infection through dodgy websites or adverts on legitimate websites.
- Password hacks: Hackers use software to hack your password and then have access to your information.
- Denial of Service (DoS): A DoS attack focuses on disrupting the service to a network. Hackers send high volumes of data or traffic through the network (i.e. making lots of connection requests), until the network becomes overloaded and can no longer function.
How do I prevent a cyber attack?
Emails:
Phishing/malicious emails usually try to convince you they are from a trusted source:
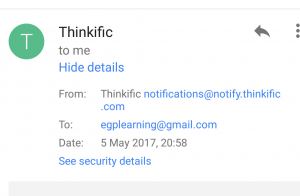
- Look at the sender’s email address: is it incorrectly spelt or does it have an unusual ending? If unsure click on the ‘view details’ or similar section to inspect the email address as shown in the images below:
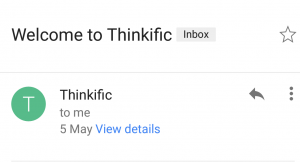
click on ‘view details’:
- In some cases you may see further information by clicking on security details. If it seems suspicious, delete the email.
- Be aware that email addresses can be faked.
If an email is from an unknown source or you’re not sure it’s genuine:
- Don’t reply- DO NOT FORWARD and NEVER use reply all. In Nov 2016 a simple ‘reply all’ action on an email led to marked spamming as people replied to ask to be deleted from the trail which led to temporary slow down and closure of the nhs.net system.
- Mark it as spam and delete it.
- If you feel it might be genuine and you might need to respond to it, create a new email and respond to a recognised address that you have used before, or access the help section on a recognised website.
- Don’t click on embedded links. If it’s a site you already use especially financial institutions, go direct to it from your bookmark/favourites.
- Don’t open attachments, and don’t choose ‘download images’.
Web browsing:
If your browser or anti-virus pops up warnings – heed them. Don’t just click through and hope for the best.Do not click on adverts. They may contain malware, even on legitimate web sites.Do not enable Flash, unless you’re sure the content you want to see is legitimate.
Transferring data:
Use secure encrypted USB sticks which are password protected and do not share them. This should be in your local information governance guidance.
Use effective passwords:
In the NHS many will be aware of the use of complicated requirements and regularly changing your password.
Follow these simple rules:
- Have a minimum length of 10 characters. 12 would be better.
- Use a mixture of capitals, numbers, and symbols like */<>-+
- To make your password memorable use a phrase that is unique to you. For example your parent’s name followed by your date of birth is a start but still at risk as it involves information that can be discovered. Alternately, use a constant with a variable like your favourite band, with numbers instead of letters combined with the current Wimbledon winner is more secure i.e. N1rv4n4-W1ll14ms.
- For an ultra-secure password use an annotated passphrase. For example: ‘This year I went on holiday to Paris and spent £100 per night on the hotel’ becomes: ‘Ty1wohtP&s£100/noth’ – hack that! Alternate examples are the first line of your favourite song or a meaningful phrase to you.
- Do not use the same password for everything. If you do get hacked it means the hackers will have access to all the sites you use. I often use one password for work, one for personal, one for banking and another two for social media.
- If able use a password manager. These are websites or apps that allow you to use a master password like 4. but then creates secure passwords that are random for each site that you use. It means you need only one ultra-secure password to manage your networks. Please note these may not work on NHS computers. Examples are Lastpass, SafeIncloud, TrueKey and Keepass.
- If the above seems complicated, simply use a password protected notepad app in your phone like Evernote or ColorNote to keep a list of your passwords for each site that you use. With your mobile phone unlock (you really should use one) and the password on the app, it provides double security for your information. For those working in the NHS given the number of various systems we use (email, patient health record, lab test access/request systems etc) this can be a practical solution in addition to the above.
If you think you have been attacked
Switch off your computer and unplug from the mains. If a mobile switch it off/ remove battery if able.Contact your IT support organisation.
Top Tips
- Be safe, if it looks unusual or too good to be true be extra wary
- Never click a link in an email unless you trust the source 100%, in preference go to the site direct and log in.
- Do not use ‘reply all’, especially to exclude yourself from an email trail. Just delete.
- Use secure passwords as above.
- Follow your local information governance guidance.
For more information or resources follow our blog.
| Hussain Gandhi | |
| GP, tech enhancer, Timelord Istari | |
| eGPlearning | |
| p: | 0115 9999999 |
| w: | www.egplearning.co.uk e: [email protected] |